
Ensuring Security & Compliance in AWS DevOps Pipelines
In today’s software-driven economy, DevOps has become the engine for innovation, enabling teams to release software faster and more reliably. But with speed comes risk. Misconfigurations, insecure code, and unchecked changes can create vulnerabilities and compliance issues. That’s where secure DevOps (DevSecOps) steps in—integrating security and compliance as native parts of the software delivery pipeline.
AWS provides a robust ecosystem for DevSecOps, allowing teams to embed security controls into every stage of their CI/CD workflows. This blog covers in-depth best practices, real-world use cases, tools, and implementation strategies to help you build secure, compliant AWS DevOps pipelines.
The Need for Security in AWS DevOps
DevOps accelerates software delivery by automating development, testing, and deployment. However, traditional security practices often lag behind this speed. Manual reviews and bolt-on security checks don’t work in this automated world.
That’s why security must “shift left”—moving earlier into the development lifecycle. Instead of being a final check, security should be continuous and automated, just like your builds and tests.
Key Drivers:
- Data Breaches: Misconfigured S3 buckets or over-permissive IAM roles can expose sensitive data.
- Compliance Pressures: Regulations like GDPR, HIPAA, PCI-DSS, and SOC 2 require strict security controls.
- Expanded Attack Surface: Containerized, microservices-based apps introduce complex dependency chains.
- Multi-Region and Multi-Account Complexity: As deployments grow, so does the need for centralized control.
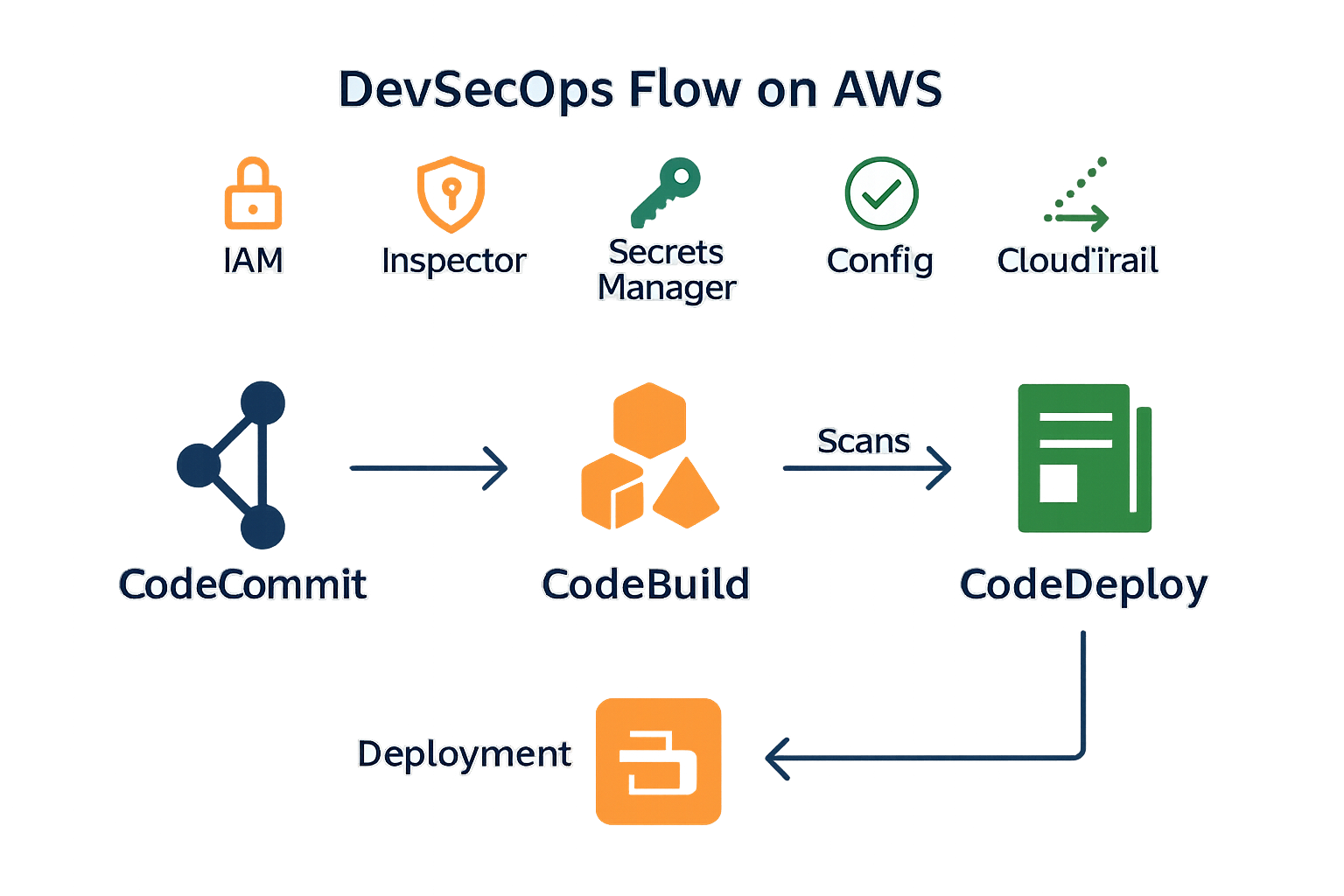
AWS Tools for DevSecOps
AWS offers native tools to embed security into DevOps workflows:
| Area | Tool | Purpose |
|---|---|---|
| Identity Management | IAM, SCPs, AWS SSO | Least privilege, account isolation |
| Secrets Management | Secrets Manager, Parameter Store | Securely manage secrets and credentials |
| Infrastructure Security | AWS Config, CloudFormation Guard | Enforce compliance, detect drift |
| Compliance | AWS Audit Manager, Security Hub | Automate evidence collection and risk assessment |
| Threat Detection | GuardDuty, Inspector, Detective | Identify and respond to threats |
| Logging & Monitoring | CloudTrail, CloudWatch, X-Ray | Full visibility and traceability |
| CI/CD Automation | CodePipeline, CodeBuild, CodeDeploy | Automate builds, tests, and deployments |
Best Practices for Secure DevOps Pipelines on AWS
Real-World Case Studies
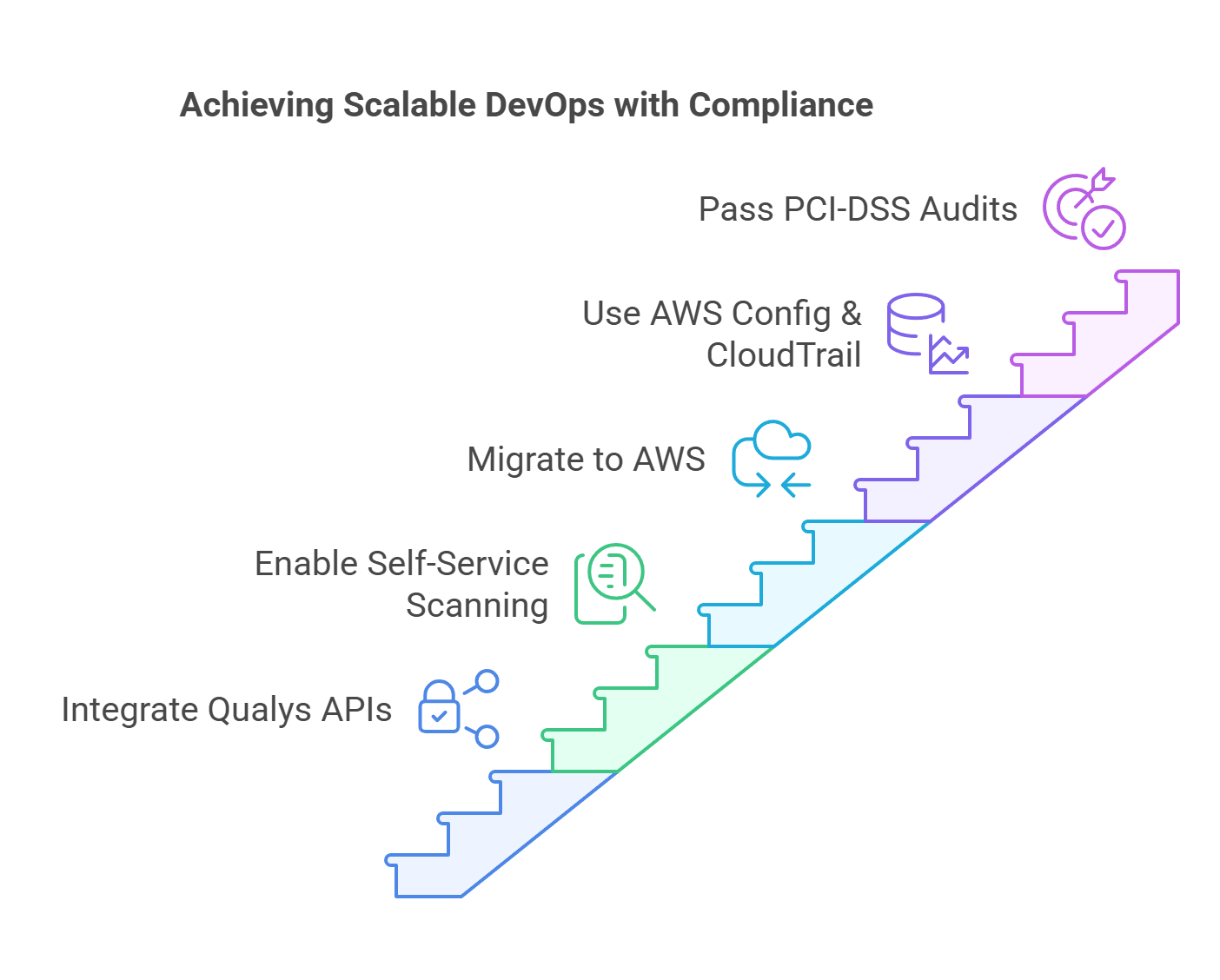
Case Study 1: Capital One — Secure DevOps at Scale with PCI-DSS Compliance
Challenge: Capital One aimed to scale its DevOps transformation while maintaining PCI-DSS compliance. Manual security evaluations for AMIs slowed down delivery and increased risk.
Solution:
- Integrated Qualys APIs for automated security scanning of AMIs and containers.
- Enabled self-service scanning by developers to reduce bottlenecks.
- Migrated infrastructure to AWS, using EC2, RDS, and Lambda with automated IAM access control.
- Leveraged AWS Config and CloudTrail for continuous monitoring and compliance.
Impact:
- Passed PCI-DSS audits with reduced manual overhead.
- Shifted security ownership to development teams.
- Improved deployment velocity and reduced vulnerabilities at scale.
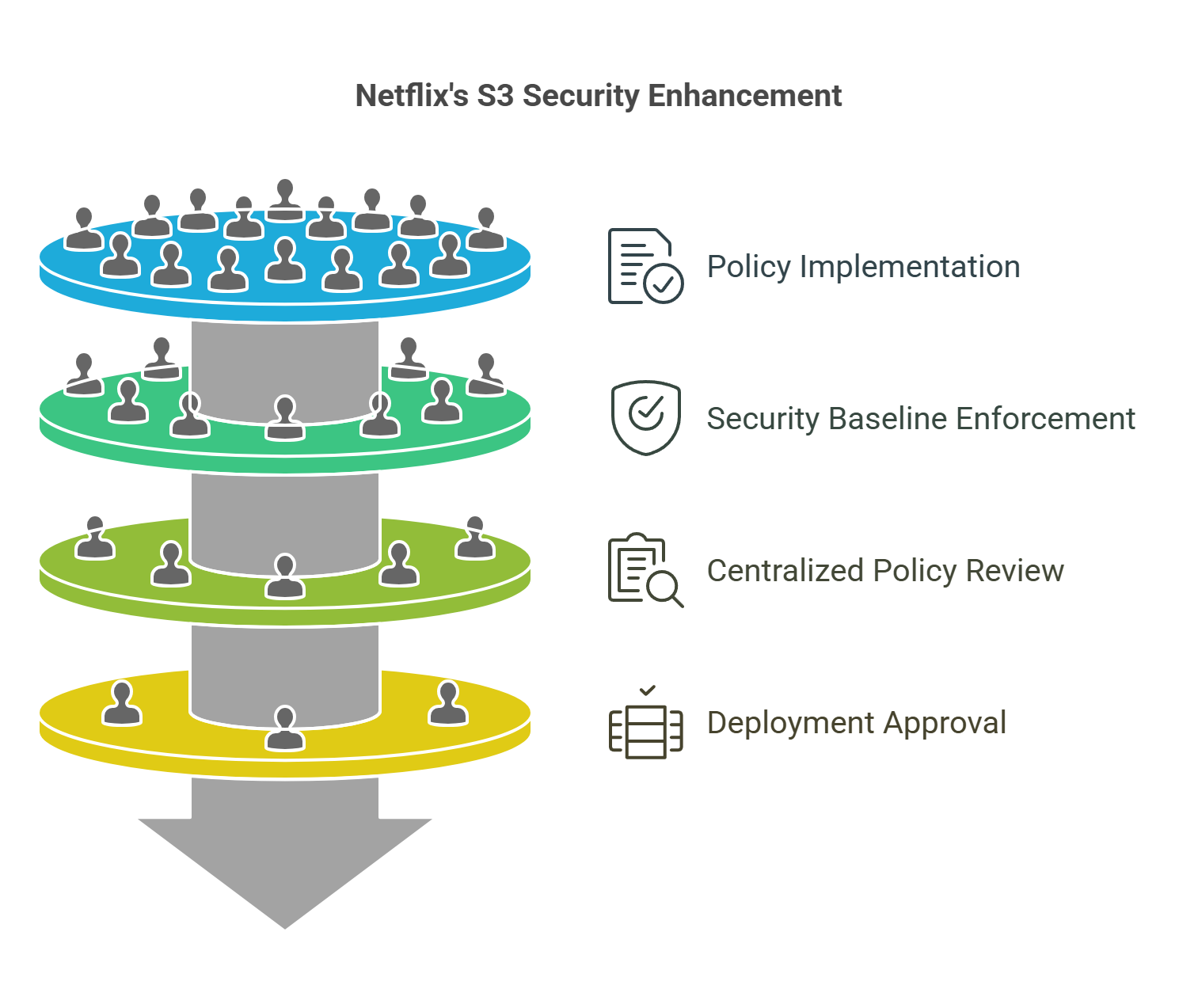
Case Study 2: Netflix Prevents S3 Misconfigurations at Scale
Challenge: As a global content platform, Netflix manages thousands of cloud resources, including S3 buckets. Preventing accidental data exposure was critical, especially as teams rapidly deployed infrastructure via automation.
Solution:
- Netflix implemented organization-wide policies using AWS Config rules such as s3-bucket-public-read-prohibited and s3-bucket-public-write-prohibited.
- They used AWS CloudFormation Guard to enforce security baselines across all IaC templates.
- S3 bucket policies were centrally reviewed through IAM Access Analyzer and CodePipeline included approvals for production deployments.
Impact:
- Netflix successfully reduced misconfigured S3 buckets to zero across all environments.
- Teams received instant feedback through failed pipeline stages when IaC templates violated S3 access policies.
- Combined use of automation and native AWS security tools resulted in consistent compliance across multi-account, multi-region deployments.
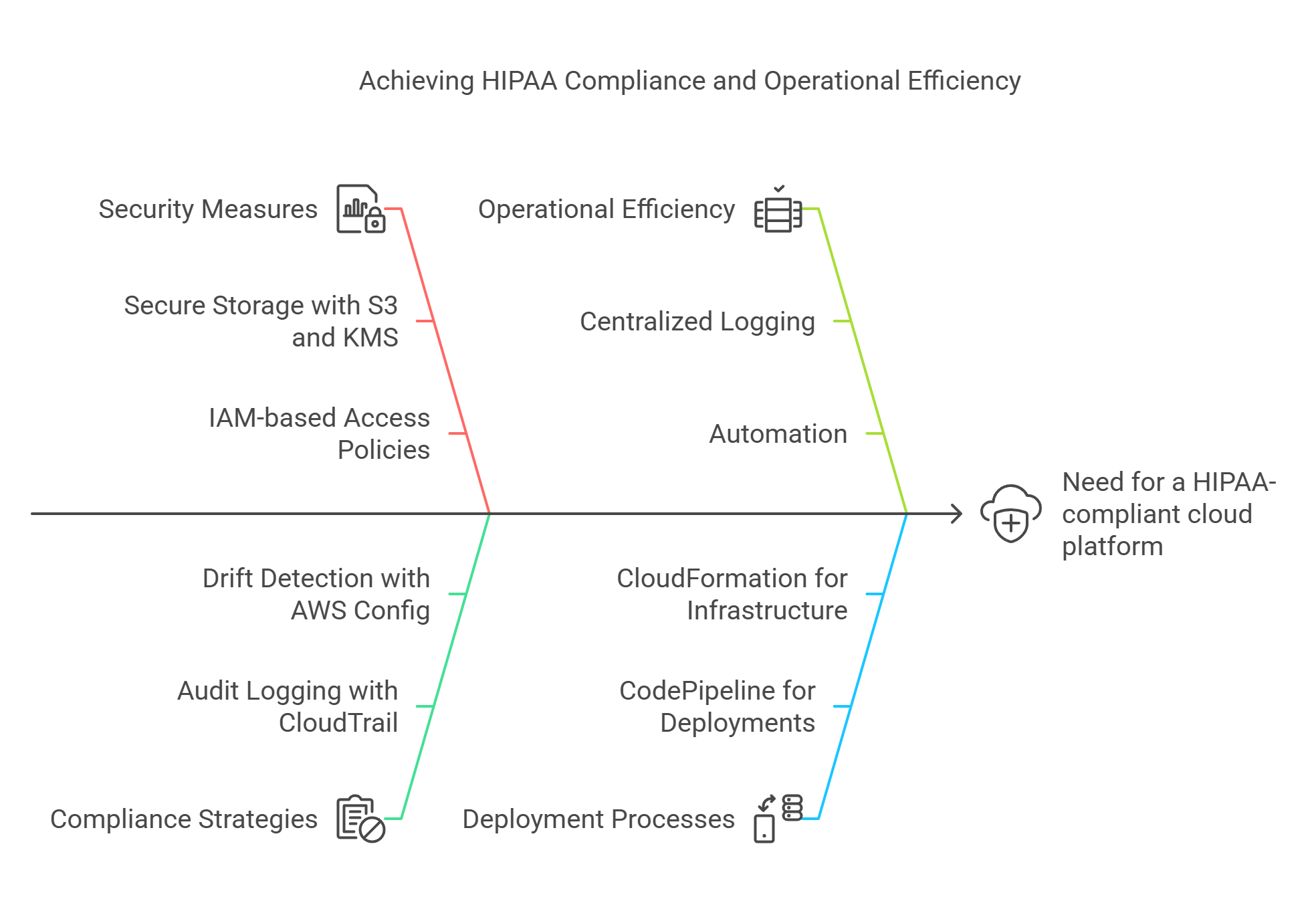
Case Study 3: Philips Builds HIPAA-Compliant Healthcare Platform on AWS
Challenge: Philips needed a HIPAA-compliant cloud platform to support global healthcare apps, ensuring secure patient data handling and operational scalability.
Solution:
- Built HealthSuite Digital Platform (HSDP) on AWS, using S3 with KMS for secure storage.
- Enforced IAM-based access policies for services and developers.
- Implemented CloudTrail and AWS Config for audit logging and drift detection.
- Used CodePipeline and CloudFormation for secure, repeatable deployments.
Impact:
- Achieved HIPAA compliance and reduced time-to-market by 40%.
- Centralized logging and automation reduced operational overhead by 30%.
- Enabled rapid global deployment of new healthcare apps while ensuring compliance.
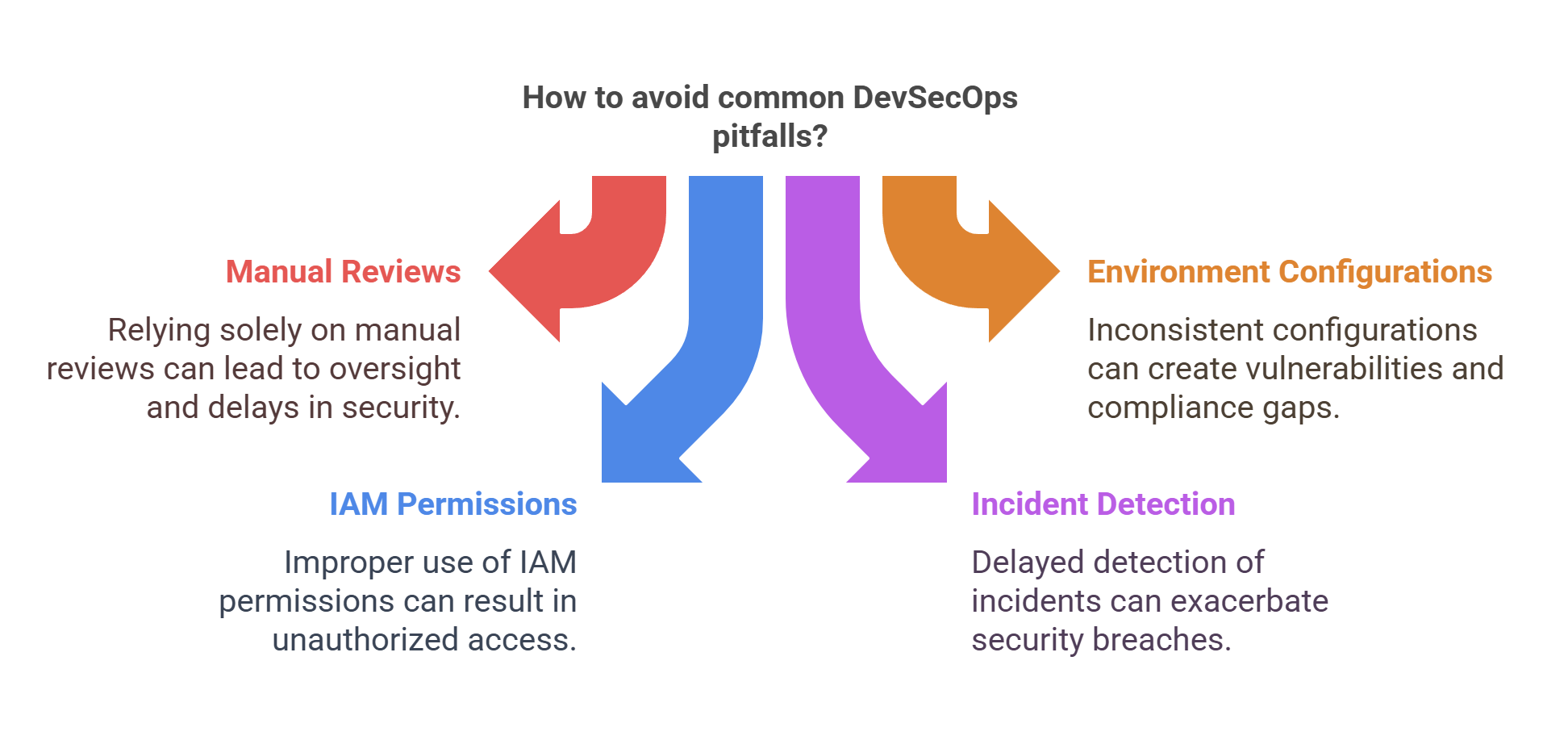
Common Pitfalls in AWS DevSecOps
Even with the best tools, teams often fall into traps that compromise security or delay compliance readiness. Here are some of the most common mistakes:
AWS Security & Compliance Tool Comparison
Choosing the right mix of AWS-native and third-party tools can make or break your security and compliance strategy. Here’s a breakdown of what to use and when:
| Use Case | AWS Native Tools | Third-Party Alternatives |
|---|---|---|
| IAM Management | AWS IAM, SCPs, SSO | Okta, Auth0 |
| Secrets Management | Secrets Manager, SSM Parameter Store | HashiCorp Vault |
| Vulnerability Scanning | Amazon Inspector | Snyk, Aqua Security, Qualys |
| Infrastructure as Code Security | CloudFormation Guard, AWS Config | Checkov, Terraform Sentinel |
| CI/CD Security Integration | CodeBuild, CodePipeline | Jenkins, GitHub Actions with security plugins |
| Threat Detection | GuardDuty, Security Hub | Palo Alto Prisma Cloud, Lacework |
| Compliance Reporting | AWS Audit Manager | Drata, Vanta |
Each of these tools has strengths. AWS-native options integrate tightly and scale easily within your cloud environment. However, third-party solutions often provide deeper functionality or cross-cloud coverage, useful in hybrid or multi-cloud environments.
To maximize effectiveness:
- Start with native tools for fast, cost-effective setup.
- Layer in third-party tools for advanced scanning or cross-cloud visibility.
- Use integrations (like sending Security Hub findings to Jira or Slack) to drive faster response.
| Metric | Ideal Target | AWS Tool |
|---|---|---|
| Mean Time to Detect (MTTD) | <10 minutes | GuardDuty, CloudWatch |
| Mean Time to Remediate (MTTR) | <30 minutes | Lambda, Security Hub |
| Secrets Exposure | Zero plaintext | Secrets Manager |
| IAM Privilege Overlap | <5% | IAM Access Analyzer |
| CI/CD Security Integration | CodeBuild, CodePipeline | Jenkins, GitHub Actions with security plugins |
| Drift Detection | Zero critical drifts | AWS Config, CloudFormation |
Implementation Roadmap
Security in Multi-Account AWS Environments
As organizations scale their AWS footprint, many adopt a multi-account strategy for isolation, security, and cost management. But managing security across accounts introduces new complexity.
Challenges:
- Visibility gaps between dev, staging, and prod accounts
- Inconsistent IAM roles and security controls
- Difficulty enforcing org-wide compliance rules
Best Practices:
- Use AWS Organizations to centrally manage accounts, apply Service Control Policies (SCPs), and consolidate billing.
- Centralize logging from all accounts using a designated log archive account. Forward CloudTrail, VPC Flow Logs, and GuardDuty findings here.
- Standardize IAM roles using AWS SSO or IAM Identity Center. Assign access based on job function, not environment.
- Use Security Hub and Config Aggregator to view compliance and findings across all linked accounts.
- Automate account bootstrapping with AWS Control Tower to apply baseline controls, tagging policies, and governance frameworks.
By securing the management layer, teams can scale securely without losing oversight or consistency.
Implementing Zero Trust in AWS DevOps Pipelines
Zero Trust is a security model that assumes no component inside or outside your network is trustworthy by default. In AWS DevOps, adopting Zero Trust means validating every user, workload, and resource request—constantly
Core Zero Trust Principles:
- Verify explicitly: Use strong authentication, least privilege, and session-based access.
- Limit blast radius: Use micro-segmentation to reduce lateral movement.
- Assume breach: Monitor, log, and inspect continuously.
AWS Implementation Practices:
- IAM Condition Keys: Enforce context-aware access (e.g., aws:SourceIp, aws:UserAgent, aws:MultiFactorAuthPresent).
- Session Policies: Restrict permissions dynamically at session level using sts:TagSession.
- VPC Service Controls: Isolate sensitive workloads via private subnets, VPC endpoints, and no public IPs.
- EKS with IRSA: Ensure pods use dedicated IAM roles with only the permissions required for their job.
- CloudTrail & GuardDuty: Continuously log API activity and detect suspicious behavior across accounts.
Example: Moderna’s Vaccine Platform
Moderna, running on AWS, adopted Zero Trust to secure its COVID-19 vaccine research data. It used:
- IAM roles with strict session policies
- Private VPCs with zero public IP usage
- Amazon Macie to scan data access patterns
This helped Moderna scale securely during intense data-sharing cycles without risking exposure.
Adopting Zero Trust inside DevOps pipelines minimizes risks and ensures workloads operate with maximum visibility and least privilege.
Real-Time Threat Response Strategies with AWS
Example: Capital One Automates Threat Isolation
Capital One integrated Amazon GuardDuty and AWS Lambda to detect and respond to high-risk IAM activity. For example, when GuardDuty flagged an unauthorized console login from an unusual IP, an EventBridge rule triggered a Lambda function that immediately disabled the IAM user, logged the action in CloudTrail, and sent alerts to Slack and Jira.
This automation cut their mean time to respond (MTTR) from hours to minutes and helped them meet internal compliance SLAs for incident response.
Example: Zocdoc Quarantines EC2 with Systems Manager
Zocdoc uses Amazon GuardDuty and AWS Systems Manager to respond to compromised EC2 instances. When GuardDuty detects malware or crypto-mining behavior, EventBridge triggers a Systems Manager Automation runbook that isolates the EC2 instance in a dedicated VPC, applies restrictive security groups, and captures a memory dump for forensic analysis.
By removing human bottlenecks and enabling forensics post-isolation, Zocdoc improved incident handling without sacrificing investigation capabilities.
Threat detection is critical—but so is fast response. With the right setup, AWS lets you automate actions that block, isolate, or remediate issues as they happen.
Key Concepts:
- Detection: Identifying risky behavior or anomalies (e.g., failed logins, unusual S3 access)
- Correlation: Linking alerts to resources, users, or patterns
- Response: Automatically or manually taking action to mitigate risk
AWS Services for Real-Time Response:
- Amazon GuardDuty detects threats such as crypto mining, port scans, or compromised credentials.
- Amazon Detective helps investigate root cause and resource relationships.
- Amazon EventBridge triggers workflows in response to findings (e.g., isolate EC2 instance on threat detection).
- AWS Lambda enables automated responses—like revoking keys, blocking IPs, or sending Slack alerts.
- AWS Systems Manager can quarantine instances, patch them, or run scripts without SSH access.
Example Response Flow:
- GuardDuty detects a suspicious port probe.
- EventBridge triggers a Lambda function.
- Lambda tags and isolates the instance, sends a Slack alert, and notifies Security Hub.
Automated incident response reduces time to contain threats and limits impact, without requiring human intervention in every case.
Modern software teams can’t afford to choose between speed and security. With AWS, you can embed DevSecOps into every part of your pipeline—ensuring resilience, compliance, and peace of mind.
Start small: secure your IAM and secrets. Then scale up with infrastructure scanning, real-time threat detection, and automated compliance checks.
Accelerate Your DevSecOps Journey with CloudJournee
Ready to build secure, compliant, and high-performing AWS DevOps pipelines?
CloudJournee offers a Free DevSecOps Assessment to help you:
- Identify security gaps in your current AWS CI/CD pipeline
- Evaluate IAM, secrets, infrastructure, and compliance automation maturity
- Receive actionable recommendations and quick wins tailored to your business
Our AWS-certified experts work with startups, scale-ups, and enterprises to optimize cloud operations, embed security, and simplify compliance.
📩 Book Your Assessment now and see how CloudJournee can help your team move faster—without compromising security.
Want to know how secure your pipeline really is? Schedule a Free DevSecOps Assessment with CloudJournee. We’ll help you pinpoint gaps, fix weaknesses, and launch faster—with confidence.


